SAP GRC Access Control Explain
SAP GRC Access Control consists of the following modules:
- Compliant User Provisioning (CUP)
- Risk Analysis and Remediation (RAR)
- Enterprise Role Management (ERM)
- Superuser Privilege Management (SPM)
Compliant User Provisioning (CUP)
CUP provides the workflow engine to drive compliant user and role maintenance processes within the SAP environment. These processes are auditable and verifiable, with clear, configurable processes for approval, SoD checking and provisioning.
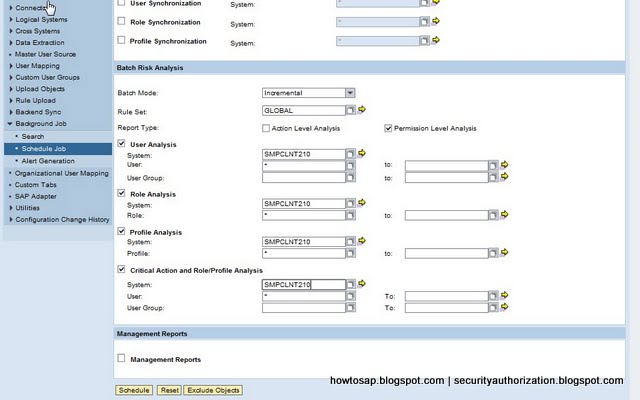
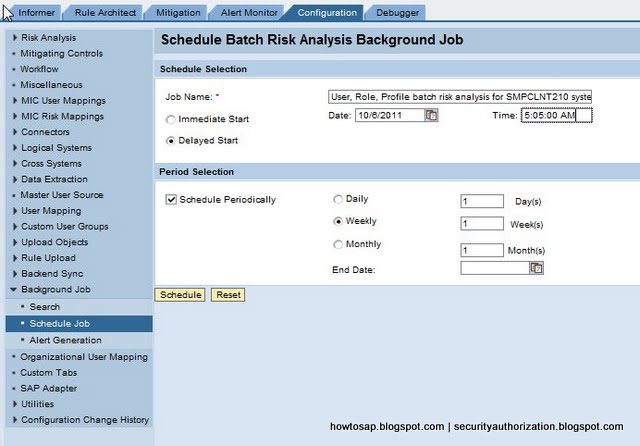
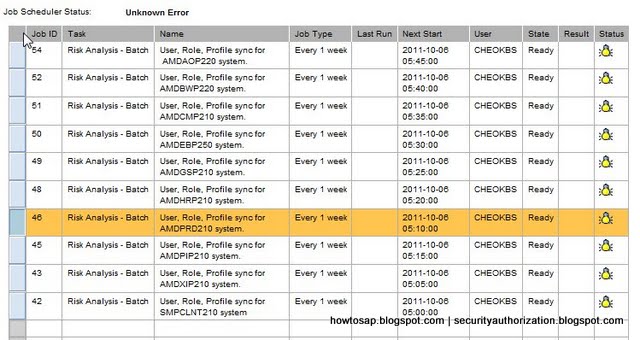
Risk Analysis and Remediation (RAR)
RAR is the repository for definitions of SOD (segregation of duties rules). As well as using the rules to check if user and role administration activities could introduce risks to your business, RAR reports on the risks within the system – presenting them in a graphical format within a web browser.
Enterprise Role Management (ERM)
ERM rigorously applies naming conventions and validations to role creation, reducing management effort and the risk of segregation of duties violations. To use ERM you have to define structured working methods.
Superuser Privilege Management (SPM)
Previously known as Firefighter, SPM lets you assign 'emergency user' status to normal support users, giving them extended access for exceptional circumstances. A notification is linked to the use of this extended access. And all activities are logged during its use to reduce the risk of unauthorised activities taking place. SPM is one of the simplest Access Control components to deploy.
Continue Reading