How to create User in SAP HANA - Assign Role and Activate User
SAP HANA Security is to protect important data from unauthorized access and ensures that the standards and compliance meet as security standard adopted by the company.
SAP HANA Provide following security-related feature –
- User and Role Management
- Authorization
- Authentication
- Encryption of data in Persistence Layer
- Encryption of data in Network Layer
CREATE USER IN SAP HANA
- Create User in SAP HANA- only database user with ROLE ADMIN privileges can create user and role in SAP HANA.Step 1) To create new user in SAP HANA Studio go to security tab as shown below and follow the following steps;
- Go to security node.
- Select Users (Right Click) -> New User.
Step 2) A user creation screen appear.- Enter User Name.
- Enter Password for the user.
- These are authentication mechanism, by default User name / password is used for authentication.
2. Define and Create Role
A role is a collection of privileges that can be granted to other users or role. The role includes privileges for database object & application and depending on the nature of the job.
It is a standard mechanism to grant privileges. Privileges can be directly granted to the user. There are many standard roles (e.g. MODELLING, MONITORING, etc.) available in SAP HANA database.
We can use the standard role as a template for creating a custom role.
A role can contain following privileges –
- System Privileges for administrative and development task (CATALOG READ, AUDIT ADMIN, etc.)
- Object Privileges for database objects (SELECT, INSERT, DELETE, etc.)
- Analytic Privileges for SAP HANA Information View
- Package Privileges on repository packages (REPO.READ, REPO.EDIT_NATIVE_OBJECTS, etc.)
- Application Privileges for SAP HANA XS applications.
- Privileges on the user (For Debugging of procedure).
CREATE ROLE IN SAP HANA
Continue Reading
Step 1) In this step,
- Go to Security node in SAP HANA System.
- Select Role Node (Right Click) and select New Role.
Step 2) A role creation screen is displayed.
- Give Role name under New Role Block.
- Select Granted Role tab, and click "+" Icon to add Standard Role or exiting role.
- Select Desired role (e.g. MODELLING, MONITORING, etc.)
STEP 3) In this step,
- Selected Role is added in Granted Roles Tab.
- Privileges can be assign to the user directly by selecting System Privileges, object Privileges, Analytic Privileges, Package Privileges, etc.
- Click on deploy icon to create Role.
Tick option "Grantable to other users and roles", if you want to assign this role to other user and role.
GRANT AND ASSING ROLE TO USER IN SAP HANA
STEP 1) In this step, we will Assign Role "MODELLING_VIEW" to another user "ABHI_TEST".
- Go to User sub-node under Security node and double click it. User window will show.
- Click on Granted roles "+" Icon.
- A pop-up will appear, Search Role name which will be assign to the user.
STEP 2) In this step, role "MODELLING_VIEW" will be added under Role.
STEP 3) In this step,
- Click on Deploy Button.
- A Message " User 'ABHI_TEST" changed is displayed.
RESET SAP HANA USER PASSWORD
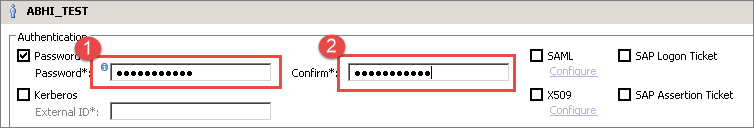
If user password needs to reset, then go to User sub-node under Security node and double click it. User window will show.
STEP 1) In this step,
- Enter new password.
- Enter Confirm password.
STEP 2) In this step,
- Click on Deploy Button.
- A message "User 'ABHI_TEST" changed is displayed.
REACTIVATE / DEACTIVATE SAP HANA USERS
Go to User sub-node under Security node and double click it. User window will show.
There is De-Activate User icon. Click on it
A confirmation message "Popup" will appear. Click on 'Yes' Button.
A message "User 'ABHI_TEST' deactivated" will be displayed. The De-Activate icon changes with name "Activate user". Now we can activate user from the same icon.
Source:
https://www.guru99.com/sap-hana-security.html
https://www.guru99.com/sap-hana-security.html